SCADA systems vulnerable in GCC, GBM annual survey recommends merger of AI and SOC

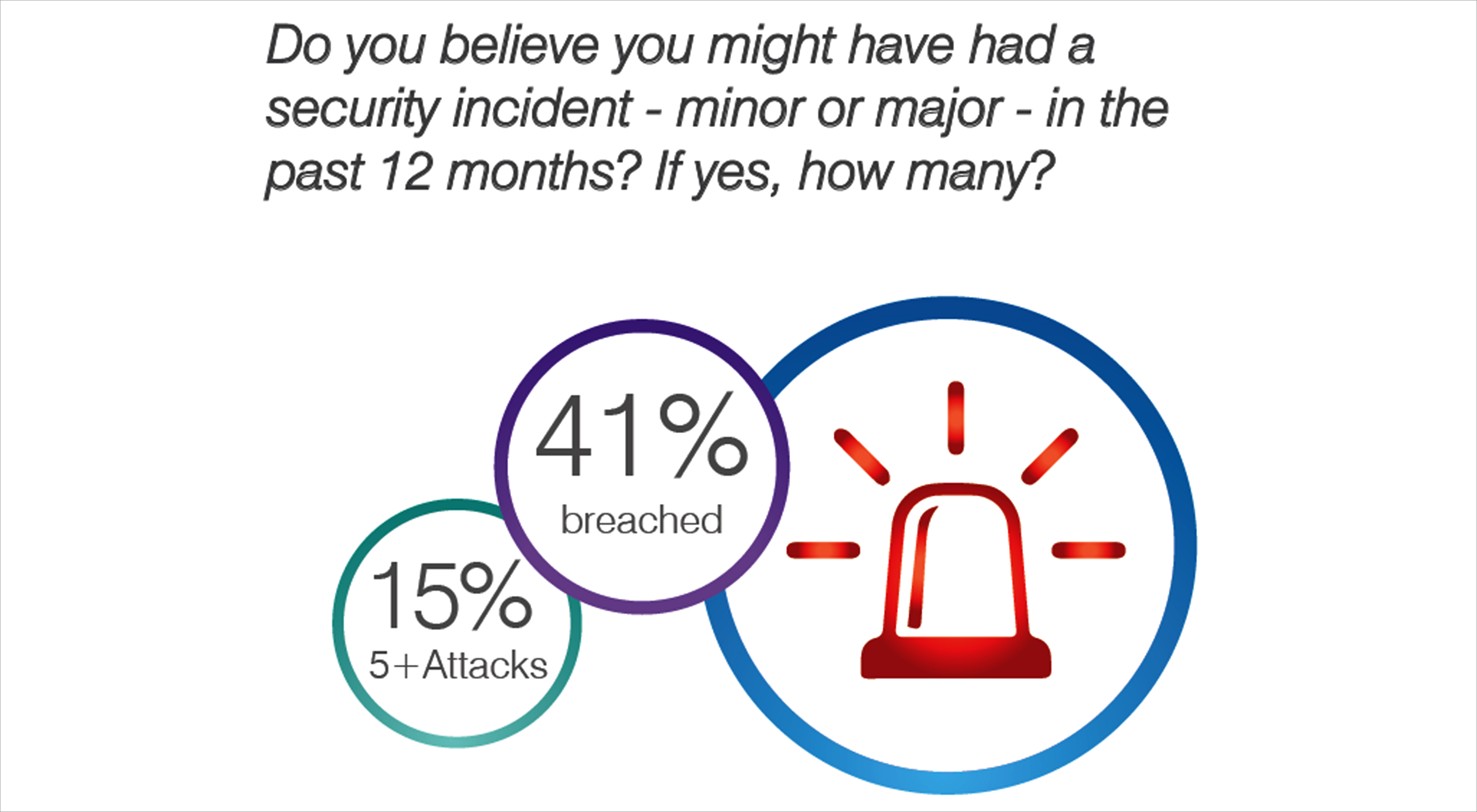
According to 7th Edition of GBM’s Annual Cybersecurity Study, conducted across UAE, Bahrain, Oman and Kuwait, 31% have already experienced attacks to their operational technology environments. The survey polled over 600 executives and IT professionals from a range of industries including IT, healthcare, education, oil and gas, hospitality, and many others.
According to Hani Nofal, Vice President, Intelligent Network Solutions, Security and Mobility, Gulf Business Machines, operational technology systems are being challenged because of the integration of SCADA systems with Internet of Things and the Internet.
Industrial control systems are the central nerve system for all manufacturing, utilities, oil and gas plants. These are the systems which operate the plants input and output, all of which are designed to work seamlessly to achieve specific measured outputs.
Computer-based supervisory control and data acquisition systems have evolved over the past 40 years from standalone, compartmentalised operations into networked architectures that communicate across large distances. In addition, their implementations have migrated from custom hardware and software to standard hardware and software platforms. However, the security envelope has not evolved with the same pace as SCADA and ICS systems.
SCADA and ICS systems and applications were designed for high resilience but not with the view of cybersecurity. SCADA and critical infrastructure systems run on the same operating platform as corporate servers and desktops. Industrial control systems send data in the clear, without any encryption or authentication.
From a cyber perspective, SCADA systems look similar to business systems like firewalls, switches, Active Directory, file and print servers, Windows Servers and workstations. However, they often lack basic protection. There is near zero visibility in SCADA environments from a threat detection perspective.
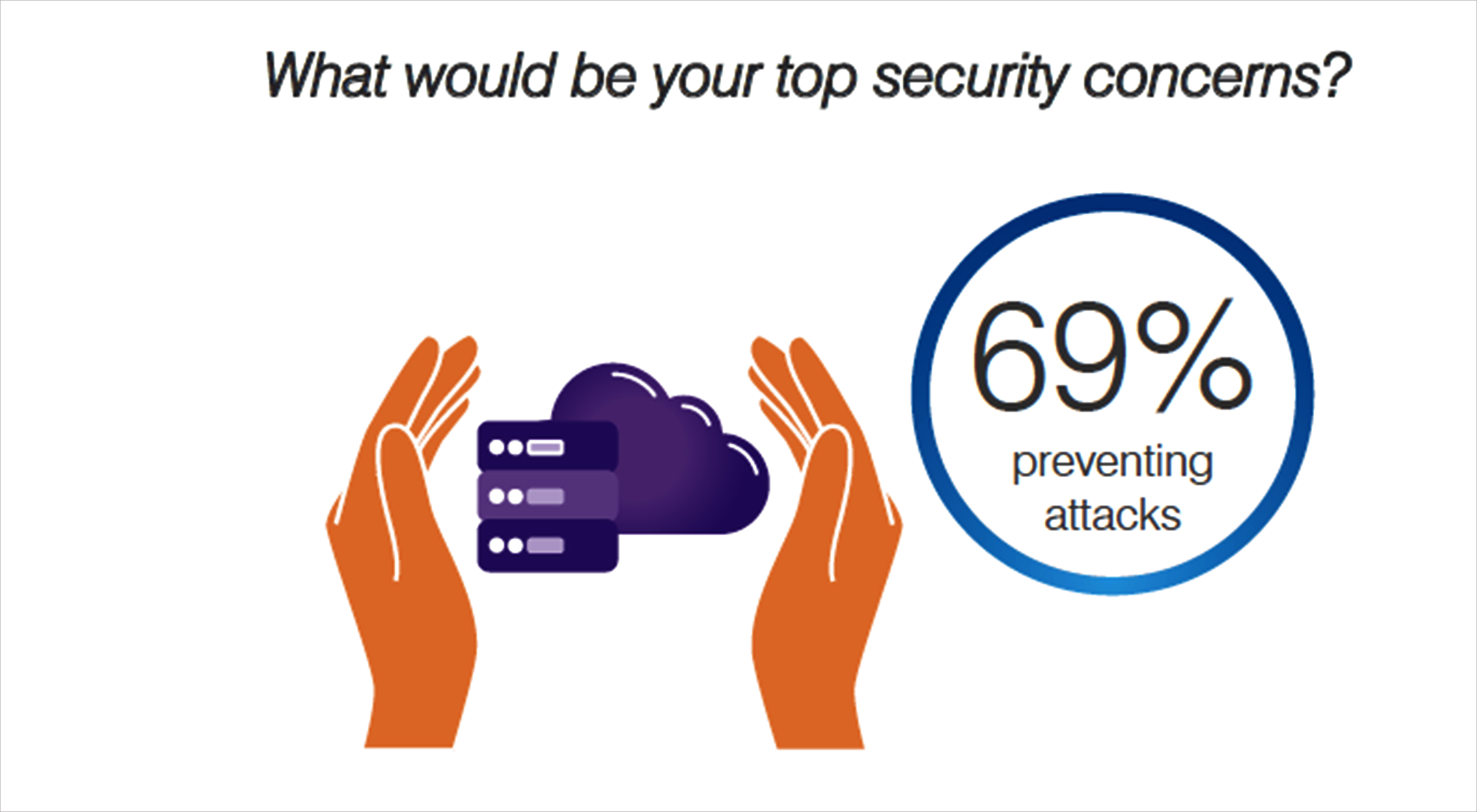
31% of organisations have already experienced attacks to their operational technology environments. There is a shift in Gulf organisations that have started taking action by deploying security controls for operational technology and developing a security strategy for prevention, detection and response.
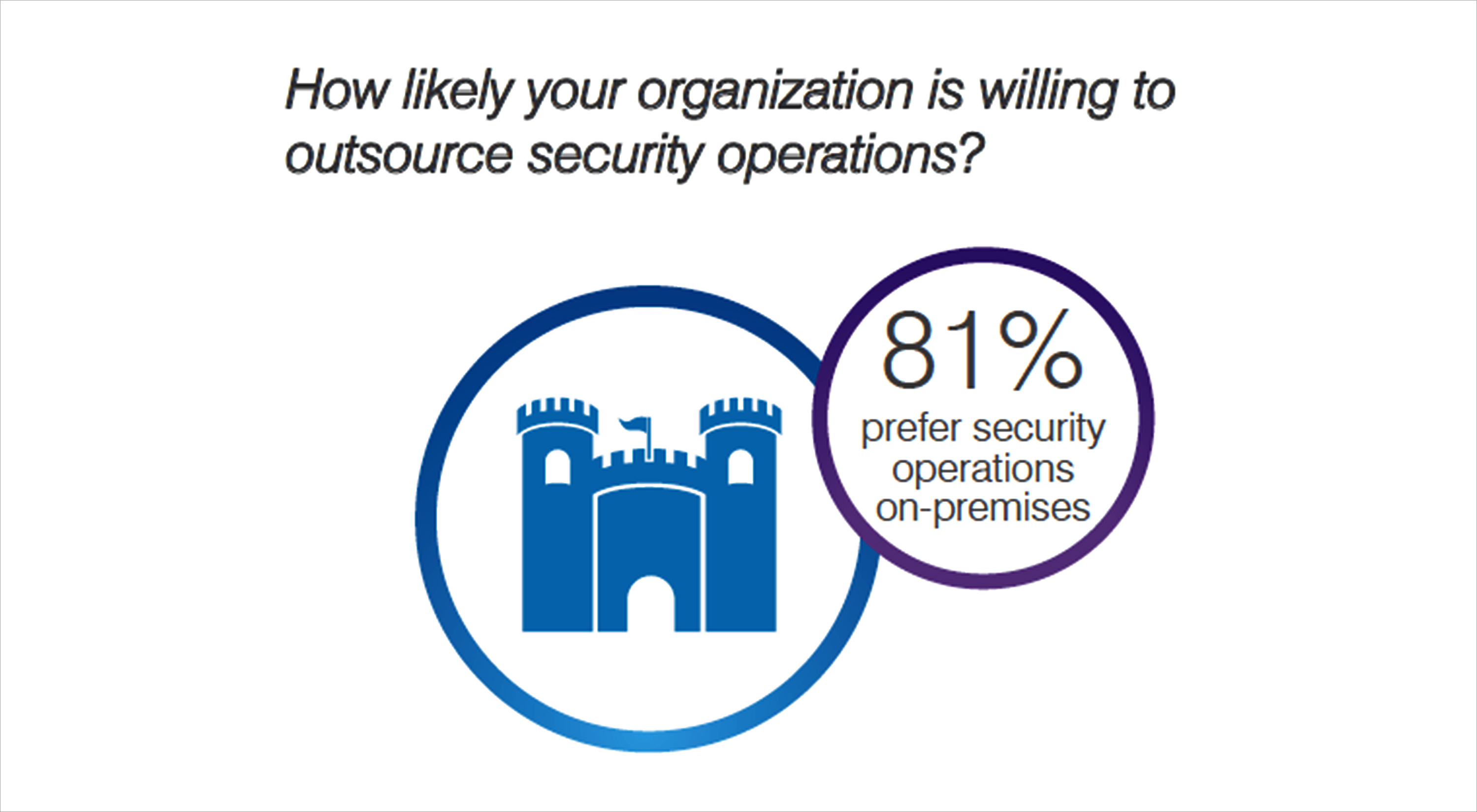
A few organisations in fact are leading the way in setting up a security operations centre dedicated for SCADA infrastructure and applications isolated from the IT environment.
Blending AI and human skills
There has been a significant increase in the development and execution of artificial intelligence and machine learning technology over the past few years. We have always talked about how everyone should improve their skills with experience – practice makes perfect – and that is the fundamentals behind machine learning, computer learning and adapting through experience.
This is why CISOs have been investigating how to use artificial intelligence to bolster their cybersecurity. Machines and technology can now be taught to teach themselves how to build models or recognise patterns and anomalies without human intervention.
Organisations can use the data from previous cyberattacks to detect and respond to newer and similar attacks their security may experience, while it can also be automated to simply watch over the network traffic, learn what is normal and use the information gathered to flag any anomalies that it considers suspicious. Detection, response and prediction are driving factors behind an artificial intelligence-based adoption with Gulf organisations.
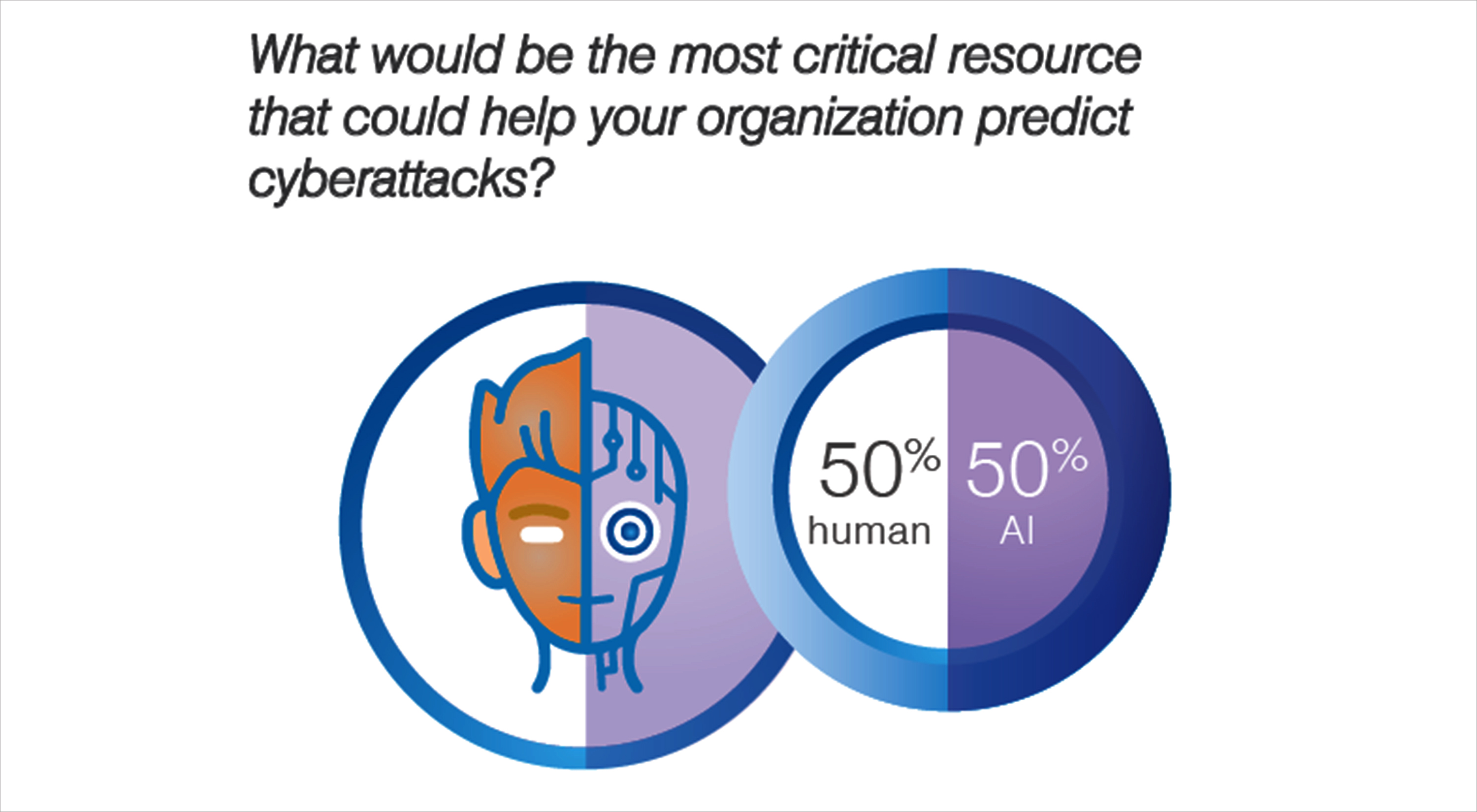
Organisations in the UAE, Bahrain, Oman and Kuwait have highlighted that a mix of artificial intelligence and human skills is the way forward to best utilise the functions of artificial intelligence or machine learning. There is an ongoing debate between cybersecurity experts on what path to take when considering the protection of their business and it appears the opinion is still split down the middle.
Organisations are now beginning to see the full benefits of utilising artificial intelligence within their cybersecurity practices as 62% of enterprises in the Gulf surveyed said they were likely to utilise artificial intelligence within 3 years, 40% of whom aim to accomplish this within a 1-2 year timespan.
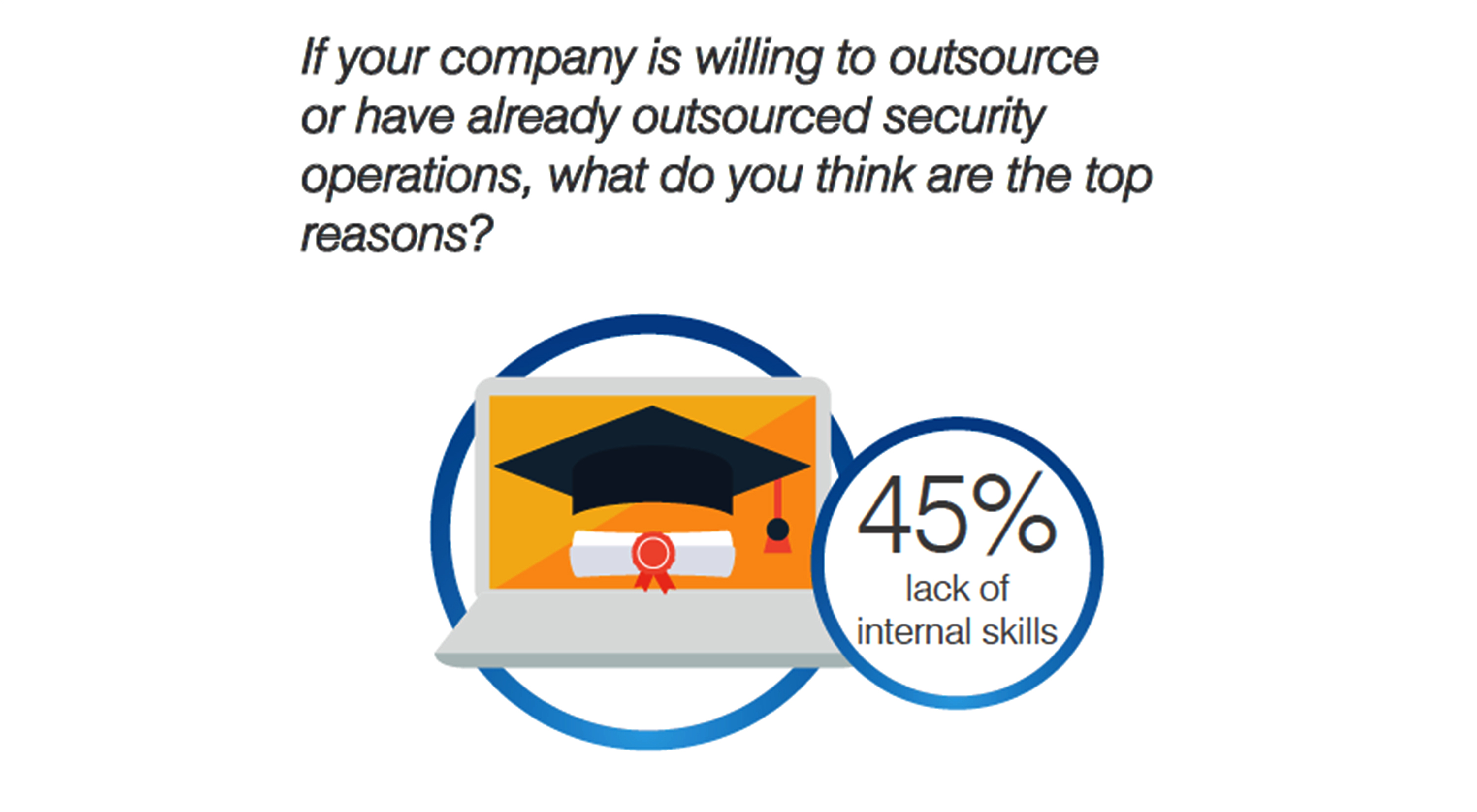
While many organisations wonder if artificial intelligence will eat into the jobs aspect, it seems far-fetched to have the same effect on cyber security. Either artificial intelligence will help in bridging the gap in human skills or create a new skillset requirement which the new generation needs to be ready with. It is unlikely that the shortage of human skills in cybersecurity will fade in the next three years.
Security operations and AI
Another, often overlooked, benefit of artificial intelligence is how much time it will free up for employees tasked with security. For the more simple attacks, the system could be programmed to deal with the situation without any guidance and instead only flag up the more extreme case to the security teams.
Taking an assume breach mentality, artificial intelligence can also be programmed to attack or breach your own systems, as any hacker would to discover vulnerabilities, sending the findings to the security team, maybe even with recommendations, so it can be patched up before it is exploited for real.
CISOs want to enhance their security, improve their operations and protect their organisation’s IT business and artificial intelligence is certainly gaining momentum in providing some much needed protection against attackers. There are always discussions about artificial intelligence bringing forth mass redundancies, but artificial intelligence needs to be applied to complement the security team and its infrastructure not replace.
The aim of artificial intelligence is to eliminate human error. However, human is the heart of not just functioning security operations centre, but a successful one. The high volume of data now being collected and stored by organisations and the sheer weight of attacks they face has made it difficult for one single solution to be the answer.
A security operations centre integrated with artificial intelligence can provide the best of both worlds, allowing a security operations centre analyst to not be overwhelmed by the constant stream of data and also consistently monitor a company’s infrastructure, flagging any major security incident that requires human intervention.
For companies uncomfortable with putting the fate of their security in the hands of unmanned machines, it is important to note that artificial intelligence still needs human feedback in order to improve the quality of its decision making. The best solution is an integrated one.
What the survey has discovered is artificial intelligence is as important as human resources in predicting cyberattacks and it is expected that mentality would be repeated in all aspects of cybersecurity. The fact is artificial intelligence and security operations centre is the future of cybersecurity and organisations in the Gulf are quickly coming to the realisation this is the direction needed to fully protect their infrastructure for the ever increasing threat of cyberattacks.
A security operations centre is a facility housing an information security team who monitor and analyse an organisation’s security on an ongoing basis. By analysing and monitoring an organisation’s network, server, data and endpoints 24×7, the security operations centre team can ensure the timely detection and response of any security incidents.
Key takeaways
- 31% have already experienced attacks to their operational technology environments.
- 31% of organisations have already experienced attacks to their operational technology environments.
- A few organisations are leading in setting up a SOC dedicated for SCADA isolated from the IT environment.
- SCADA and ICS systems and applications were designed for high resilience but not with the view of cybersecurity.
- There is near zero visibility in SCADA environments for threat detection.
- The aim of artificial intelligence is to eliminate human error.
- SOC integrated with artificial intelligence allows analysts to not be overwhelmed by data and monitor a company’s infrastructure.
- Artificial intelligence is as important as human resources in predicting cyberattacks.